Information Protection Policy


Orion is committed to protecting and managing customers' personal information and the company's critical information assets by establishing clear information security guidelines and continuously implementing security measures.
We comply with relevant regulations and regularly update our privacy policy. Our dedicated privacy officer routinely monitors personal data processing practices to ensure compliance with internal protocols. In addition, we operate advanced security solutions to prevent the leakage of core R&D assets and safeguard the company's intellectual property.
Orion Corporation
CEO Seung-Joon Lee
Information Security Policy
① Orion is committed to protecting and managing customers' personal information and the company's critical information assets by establishing clear information security guidelines and continuously implementing security measures.
[Information Security Organization]
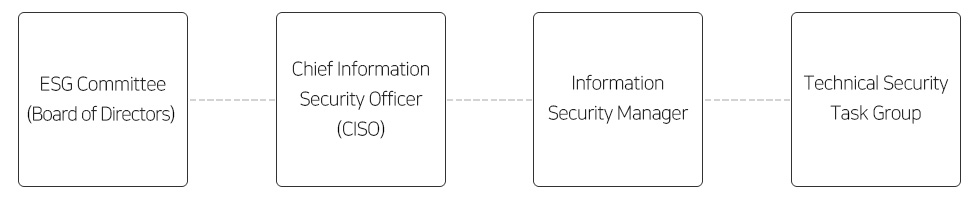
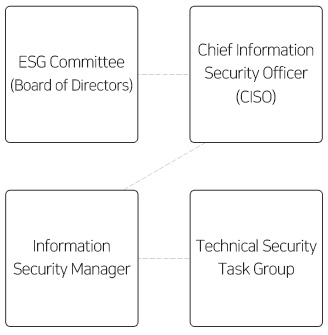
② To systematically manage customer information and corporate data assets, Orion has established internal information security regulations and operates related guidelines.
·Information Security Policy
- Internal Management Plan (Personal Information Protection Policy)
- Personal Information Handling Guidelines
- Application Security Guidelines (Secure System Development Standards)
Strengthening Information Security Practices
- To prevent the leakage of critical R&D information, a centralized document management system has been implemented.
This ensures that sensitive data is securely stored and protected from unauthorized external access.
- Regular Internal Audits are conducted to assess the status of personal information protection, and continuous improvements are made to address identified vulnerabilities.
- Ongoing training programs are provided for employees who handle personal information.
In addition, company-wide awareness campaigns are conducted through the internal groupware system to reinforce data privacy and security practices.
- To minimize system downtime, quarterly system inspections and security patches are performed.
Continuous monitoring is in place to ensure the stability and reliability of all critical systems.
- Key systems are hosted on professional cloud platforms to enhance both security and operational continuity.
These platforms provide robust security services that help address potential vulnerabilities from external threats.
- Crisis response drills are conducted regularly to ensure swift recovery in the event of a system failure or incident.

